Cryptography
Cryptography is the security cornerstone of the DF Protocol. It ensures that the computing power reported by every node is verifiable, every message is authentic, and every asset distribution requires no manual intervention.
While users and most developers do not need to master all the mathematical principles behind the protocol in depth, understanding the cryptographic primitives relied on by DF helps to more clearly recognize its security, transparency, and economic fairness.
The DF Protocol constructs a complete verifiable computing power model through rigorously designed cryptographic mechanisms. This section introduces the main cryptographic tools used by the protocol and their functions for developers, researchers, and participants.
Hash Function
Hash functions are a type of one-way function that map inputs of arbitrary length to outputs of fixed length, serving as the core tool for the DF Protocol to achieve "data tamper-proofing." All reported computing power tasks undergo off-chain hashing and timestamping before entering the on-chain verification process.Key characteristics of hash functions include:
Determinism: The same input will always produce the same output.
Collision Resistance: It is extremely difficult to find two different inputs that generate the same hash value.
Preimage Resistance: It is impossible to deduce the original input from the hash value.
Avalanche Effect: A slight change in the input will result in a completely different output.
The DF Protocol primarily adopts the BLAKE2b algorithm, which balances efficiency and security, making it suitable for computing verification scenarios in blockchain environments.
Node DH-ID (Node Encrypted Identity)
Node DH-ID is the unique identity identifier of a DF node, generated by hashing the ECDH public key. It has the following characteristics:
Decentralized generation, no registration or authorization required;
Used to bind node computing power, signatures, incentives, and governance weight;
Publicly verifiable but unforgeable.
It constitutes the identity layer foundation of the entire DF trust network.
Types of Cryptography
Cryptographic algorithms are implemented in two ways: symmetric cryptography and asymmetric cryptography.
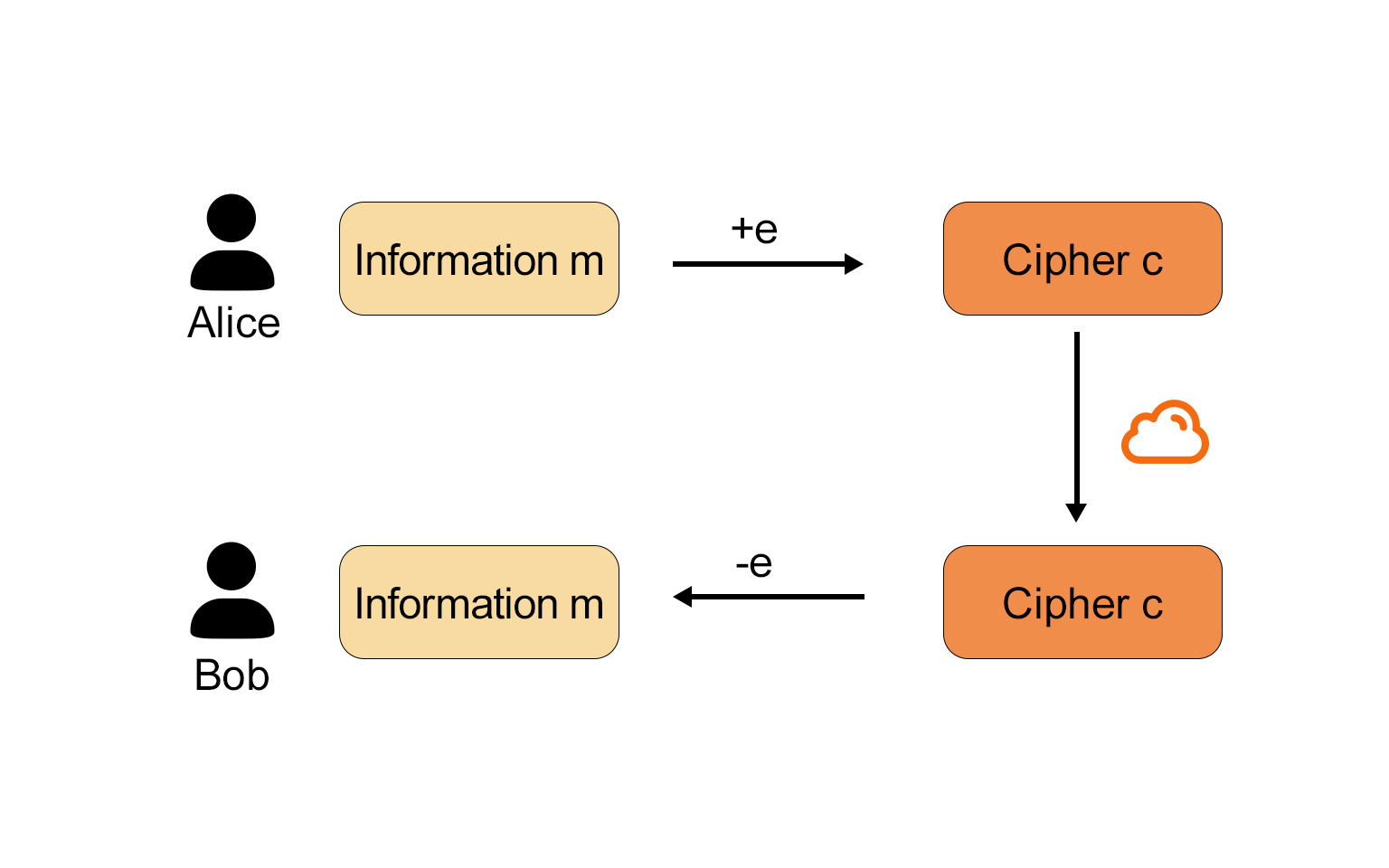
Symmetric Cryptography
Symmetric encryption is a branch of cryptography that, unlike asymmetric encryption, is not based on one-way functions. It uses the same encryption key to encrypt plaintext and decrypt the generated ciphertext.
Symmetric encryption is a historically widely used encryption method, such as the Enigma machine and the Caesar cipher. It is still widely applied today, found in both Web2 and Web3 applications. Symmetric encryption uses a single key, and the recipient must possess this key to access the encrypted information.
Advantages:
Fast and efficient when processing large amounts of data.
Requires less computational power.
Disadvantages:
Key distribution can be challenging.
Scalability issues may arise in systems with many users.
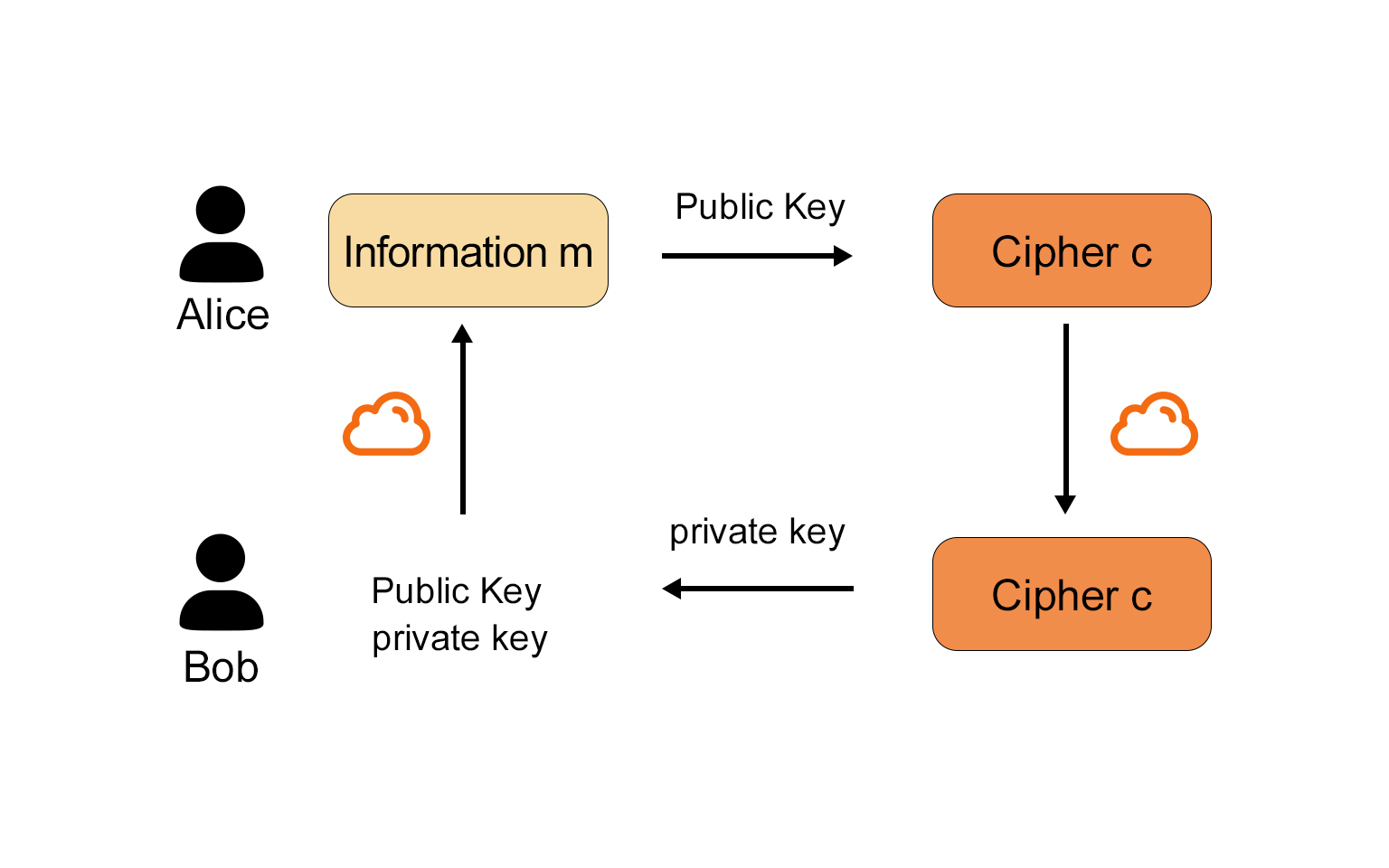
Asymmetric Cryptography
Asymmetric encryption is a cryptographic technology that uses two distinct keys (called a key pair): a public key, used to encrypt plaintext; and a private key, used to decrypt ciphertext.
The public key is used to encrypt fixed-length messages, which can only be decrypted using the recipient’s private key and sometimes a preconfigured passphrase. The public key can also be used to cryptographically verify that data was created using the corresponding private key without revealing the private key itself—for example, in digital signatures. This has obvious implications for identity, ownership, and asset management, and is widely applied in many different protocols across Web2 and Web3.
Advantages
Solves the key distribution problem.
Supports digital signatures and secure key exchange.
Disadvantages
Slower than symmetric encryption.
Requires more computational resources.
Digital Signatures
Every computing power report and communication packet is signed with the node’s private key. Signatures ensure:
The credibility of data sources;
Data remains untampered during transmission;
Node identity verification does not require a centralized account.
The DF Protocol adopts the Elliptic Curve Digital Signature Algorithm (ECDSA) for signing, boasting the advantages of a simple structure, efficient verification, and suitability for multi-party aggregation.

Hybrid Encryption Architecture
The DF Protocol adopts a classic hybrid encryption model:
ECDH: Negotiates and generates a secure session key;
AES-256: Efficiently encrypts data transmission between nodes;
Hash function: Verifies task integrity;
Digital signature: Proves identity and work validity.
This layered model balances performance and security, while reserving scalability for subsequent post-quantum encryption upgrades.
Security Guarantees
By virtue of the aforementioned cryptographic mechanisms, DF Protocol provides the following security guarantees:
Unmonitorable Communication
ECDH / AES-256 Encrypted Transmission
Unforgeable Identity
DH-ID Hash Binding + Signature Verification
Unforgeable/Non-Copyable Computation
PoSW Signature + Random Verification + On-Chain Recording
Non-Forkable/Non-Tamperable Rewards
Smart Contract Locking + Node Signature Binding
Non-Covert Manipulation of Node Control
DH-ID + Asset Association + Governance Tracking
DF is planning the following expansion directions:
Introduce Lattice-based Cryptography to implement post-quantum hybrid signatures;
Support MPC (Multi-Party Computation) and zero-knowledge proofs (ZKPs) for the verification of private computing power tasks;
Build a cross-chain DH key bridging mechanism to serve multi-chain computing power sharing scenarios.
Last updated